Given how quickly cybersecurity is changing, the threat that the Counter.wmail-service.com Trojan poses needs to be addressed very away. This sneaky virus compromises security and poses serious privacy hazards by infecting computer systems and specifically targeting users’ email services. With the help of our thorough instructions, users should be able to quickly and effectively eliminate this nasty intruder from their systems.
Understanding the Counter.wmail-service.com Trojan
It is important to understand the nature of the Counter.wmail-service.com Trojan before beginning the eradication process. This malicious malware works covertly, breaking into systems without authorization and causing significant harm.
Signs of Infection
To effectively counter the Trojan, users must be vigilant and recognize signs of infection. The following indicators may suggest a Counter.wmail-service.com infiltration:
- Sluggish Performance:
- If your system experiences slowdowns, unresponsiveness, or freezes, it may indicate malicious processes consuming system resources.
- Changes in Network Activity:
- Unusual network traffic or unexpected data usage could be a result of the Trojan communicating with remote servers.
- Frequent Freezes or Crashes:
- Trojan-induced destabilization may lead to frequent crashes or freezes in applications.
- Unauthorized Access:
- Trojans can create backdoors, allowing unauthorized access, potentially harming files without the user’s knowledge.
Methods for Effective Removal
Method 1: Utilize the Rkill Extension
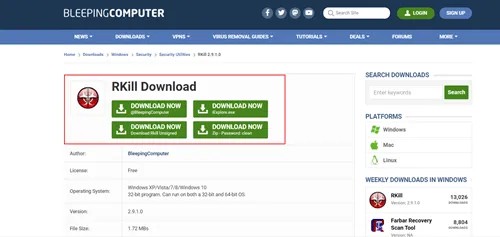
Download the Rkill extension from a reputable source, such as “BleepingComputer,” and run it to temporarily halt malicious processes.
Method 2: Uninstall Malicious Programs
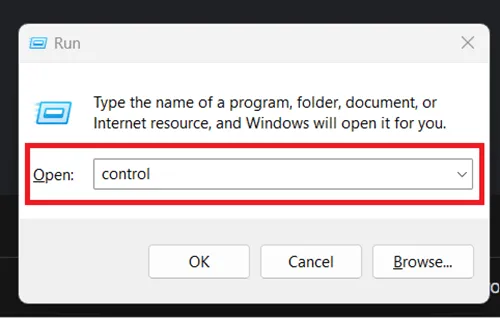
Access the Control Panel, identify suspicious programs, and uninstall them to eliminate potential sources of the Trojan.
Method 3: Remove Trojan from Windows Registry
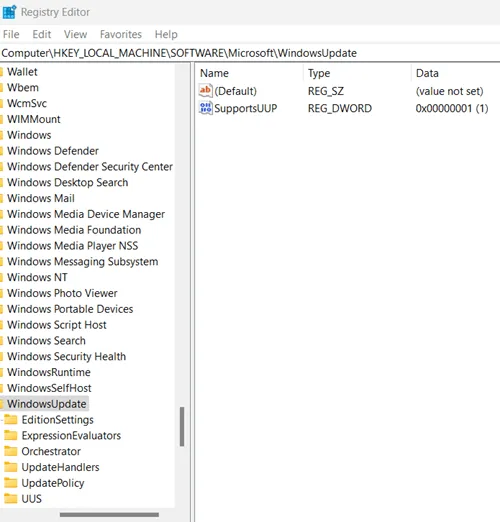
Open the Registry Editor by pressing Windows key + R, navigate to specific registry paths, and delete suspicious entries.
Method 4: Delete Malicious Files and Folders
Open the File Explorer using Windows key + E.
Search for some suspicious in different files and folders present in various locations.
Now, you need to right-click on those and delete them.
Method 5: Reset Browser Settings
If your web browser was affected previously, you should reset its settings to “default”.
Method 6: Run a Full System Scan
Utilize updated anti-malware or antivirus software for a comprehensive system scan and removal of any remaining malware.
Method 7: Update and Secure Your System
Ensure the system and security software are regularly updated. Enable automatic updates, exercise caution when downloading software, and maintain a backup of important files.
Method 8: Monitor Your System and Stay Vigilant
Regularly check for signs of malware, monitor system performance, and be cautious about granting permissions to applications. Stay informed about cybersecurity threats.
Conclusion: Safeguarding Your Digital Haven
Navigating the threats posed by the Counter.wmail-service.com Trojan requires diligence and proactive measures. By following our detailed guide and staying informed about cybersecurity best practices, users can eliminate the virus, protect sensitive information, and fortify their systems against future infections. Remember, knowledge and safe browsing habits are key to maintaining a secure digital environment.
Frequently Asked Questions (FAQs)
Does the Trojan Harm Other Devices on the Same Network?
Yes, the Counter.wmail-service.com Trojan can harm other devices on the same network, posing significant risks by exploiting vulnerabilities and utilizing shared resources.
Can Counter.wmail-service.com Trojan Steal Personal Information?
Yes, the Trojan has the potential to steal personal information, including usernames, passwords, and financial data, emphasizing the importance of its removal for data protection.
Does Removing the Trojan Restore Browser Settings?
No, removing the Counter.wmail-service.com Trojan does not automatically restore browser settings. Users should manually configure settings for a comprehensive removal and restore the browser to its initial configuration.

